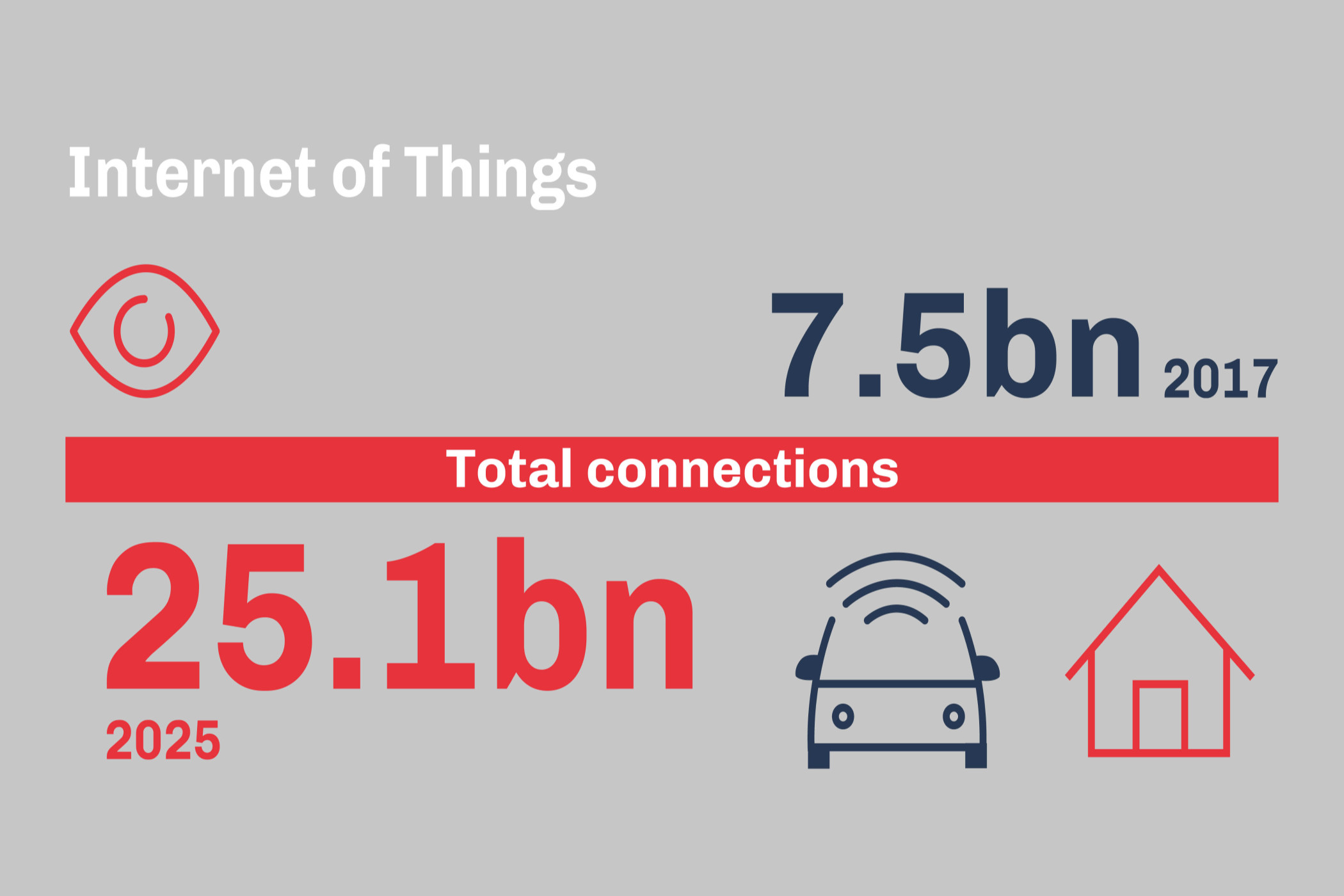
Based on the expected number of connections alone, experts predict security problems already for this year. (picture: mylk+honey)
No new technology comes without risks. Even with 5G, risk assessment and risk evaluation have long been an integral part of research, development and political discussion. The article shows how cyber security experts assess the situation and names the sectors of industry affected.
Attacks on bank infrastructures, underground trading with biometric data, increased attacks with Java script skimmers – the list of threats in the digital environment is getting longer and longer. Those who are aware of the dangers are far from protected, but they can take appropriate countermeasures.
Although security experts see the financial sector as being particularly at risk, the issue of cyber security has also reached the top of the agenda in industry, not just since prominent examples such as the Pilz company went through the press.
The teams responsible for cyber security in companies should pay particular attention to the cloud infrastructure. In addition, there are likely to be increasing risks in terms of employee access to the network, as some groups of cybercriminals have specialised in using insiders for their own purposes. Various methods – including blackmail – are used to do this.
Risks associated with 5G
Telecommunications and other mobile-related industries should also prepare for risks associated with the growing use of 5G. New threats associated with this need to be assessed and addressed, according to experts at Securelist, an information platform from Kaspersky.
They see the danger alone in the sheer number of devices and network participants to be expected. Physical access to mobile phone technology will also be more difficult to control due to the increase in mobile phone masts. More often than with 4G, these are likely to be located in public buildings, for example.
Experts believe it is conceivable that major DDoS attacks or problems in protecting an advanced network of connected devices could occur, with one device as a vulnerability leading to the crash of the entire network. In addition, 5G is developing a technology that builds on the existing infrastructure and often takes over the weaknesses and misconfigurations of existing installations.
It is also likely that the intensive use of 5G network bandwidth by IoT and M2M devices and their networking in the 5G network will reveal previously unknown problems in the design and behavior of 5G. In light of such concerns and the additional political controversy, the adoption of a zero-trust network model and rigorous quality assessment, together with regulatory compliance, would help shape the relationship between technology users and providers.
Although the detailed report at https://securelist.com/5g-predictions-2020/95386/ does not directly address the discussion about Chinese suppliers such as Huawei, it explicitly includes an appeal to those responsible to explicitly involve the authorities in order not to jeopardize technical progress in connection with 5G through security problems.







Leave A Comment