The AdaptiveMobile Security whitepaper describes the three main attack scenarios (Source: AdaptiveMobile Security)
Network slicing is supposed to make it possible to operate separate virtual 5G networks side by side. But a flaw in the security architecture makes the concept vulnerable to espionage attacks and network disruptions.
With network slicing, a mobile operator can divide its core and radio network into several different virtual blocks that have different characteristics. The same is true for campus network operators. Using this technology, for example, a network for IoT that requires low bandwidth can coexist with a real-time, low-latency, high-bandwidth network. On a third network, the plant operator grants the machine builder limited access from the outside, which allows the machine builder to perform remote maintenance but prevents access to production data.
AdaptiveMobile Security, a global mobile network security company, has now discovered a serious security problem. Attackers could exploit this security hole and trigger unauthorized data access and denial-of-service attacks between different network slices in a mobile operator’s 5G network. Enterprise customers are at risk of malicious cyberattacks, the company said.
The core of the problem
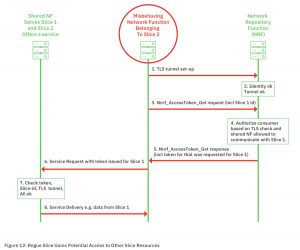
This is just one of the security issues discovered by AdaptiveMobile Security. Source: AdaptiveMobile Security
Security experts have made public a detailed description of the vulnerability. The key problem is the lack of mapping between the application and transport layer identities. An attacker could exploit this, provided they have access to the 5G Service Based Architecture. For example, a hacker who compromises an edge network function associated with the operator’s service-based architecture could grant other organizations access to the operator’s core network and individual network slices.
Other things at risk include user location tracking, plus loss of load-related information and even disruption of the operation of the slices and the network functions themselves. For the operators of a campus network, the reliability of the self-operated infrastructure is one of the key decision criteria in addition to security. Possible interruptions of a production network due to attacks from outside must therefore be avoided at all costs.
Solution digs deep into technical standards
The three main attack scenarios discovered cannot be prevented with current technologies, warns AdaptiveMobile Security. Its experts are currently working closely with the GSMA, mobile network operators and standardization bodies to solve the problem. They say this will also require further development of fundamental technical architectures to prevent active exploitation of this vulnerability.
“5G is driving the mobile industry into adopting the technology and techniques of the IT world to increase efficiency and improve functionality. However, while laudable, there needs to be a wider mindset change. When it comes to securing 5G, the telecoms industry needs to embrace a holistic and collaborative approach to secure networks across standards bodies, working groups, operators and vendors.”
Dr. Silke Holtmanns, Head of 5G Security Research at AdaptiveMobile Security
Detailed information on the research findings can be found by interested parties in the whitepaper “A Slice in Time: Slicing Security in 5G Core Networks,” which can be downloaded from AdaptiveMobile Security’s website.








Leave A Comment